Internet of Things (IOT) Security is the technology used for security and safeguarding of the connected devices and networks in the internet of things. Due to the ongoing advancements in the Information technology (IT) sector and increasing awareness about hacking, viruses etc, there has been increase in the number of cyber attacks. In order to protect the IOT devices from cyber threats, IOT security is widely deployed. The global IOT security is expected to have a CAGR of 38% during the forecast period 2016-2023. There has been an increase in the demand of IOT devices due to the increasing adoption of IOT technology. According to Phys.Org (science, research and technology churnalism website) more than 20 billion devices are expected to be upgraded to IOT technology by 2020. A number of web services such as online banking and Google, use two step authentication process to increase the security levels and prevent passwords from being hacked.
The key factor contributing to the growth of IOT security market is the increasing number of ransomware attacks on IOT devices due to which there has been a vast increase in the usage of IOT security solutions. Ransomware is a malware that locks mobile phones, computers and other connected devices or encrypts the electronic files and the user loses the access to these devices and data and demands a ransom to provide them the access back. According to Phys.Org (science, research and technology churnalism website) in May 2017, there was a large ransomware attack worldwide, named WannaCry Ransomware Cryptoworm, which mainly targeted computers functioning on Microsoft Windows OS. The files were encrypted and ransom payments were demanded in the Bit coin crypto currency by the attackers. The 3 major factors due to which IOT devices are prone to ransomware attacks are growth of IOT technology, evolution of ransomware and unawareness of risks associated with ransomware. Therefore, to mitigate the risks of ransomware attacks , new categories of security softwares based on the deception technology have been developed. Deception technology uses the fake SMB data shares to mislead the ransomware which is encrypting these dummy SMB data shares. This alerts the , cyber security teams and notifies them about the ransomware attack in order to prevent this attack and bring the organization back to its normal operations.
Source: OBRC Analysis.
The report on global IOT security market includes segmentation on the basis of security, solution and applications.
Security types included in the global IOT security market report are:
- Network security
- Endpoint security
- Application security
- Cloud security
Solutions included in the global IOT security market report are:
- Secure communication
- Device authentication and management
- Secure software and Firmware update
- Data Encryption
- Identity access management
- Others
Applications of IOT Security market include:
- Smart Manufacturing
- Connected Healthcare
- Consumer wearables
- Connected vehicles
- Smart government and defense
- Smart energy and Utilities
- Others
The global IOT Security market report has been geographically segmented into:
- North America (U.S. & Canada)
- Asia Pacific (China, India, Japan, RoAPAC)
- Europe (UK, France, Germany, RoE)
- Rest of World
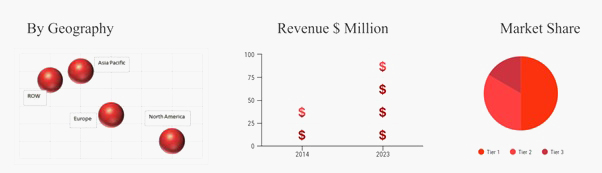
North America has the highest market share for IOT security market. Most of the major market players are headquartered in U.S. and the awareness regarding the advantages of Internet of things among the residents is contributing to its market growth. Asia Pacific is the fastest growing region in the global IOT security market. One of the driving factors is increasing Internet penetration. According to International Telecommunication Union, in Asia around half of the global internet users are present which accounted to be 1.89 billion in March 2017. Out of which China has the highest internet user base (around 670 million internet users) in 2017. Hence, the largest internet user base in Asia Pacific is contributing towards the growth of Asia Pacific IOT security market.
Global IOT security market report covers segmentation analysis of security, solutions and application. Report further covers segments of security type which includes network security, application security, cloud security and endpoint security. Among these segments, cloud security is witnessing substantial growth across different verticals with software, platform and infrastructure in demand, for sensitive data. The cloud security market is expected to expand at a CAGR of over 25% during the forecast period and reach revenue worth $13 billion by 2022. By solutions, the market is segmented into secure communication, device authentication and management, secure software and firmware update, data encryption, identity access management and others. the identity access management (IAM), is the most advantageous segment as it facilitates advanced authentication over other solution segments and enhances enterprise mobility. Whereas, applications of IOT security include smart manufacturing, connected healthcare, consumer wearables, connected vehicles, smart government and defense, smart energy and Utilities etc.
The major market players of the global IOT Security market are:
- IBM CORPORATION
- AT&T INC.
- GEMALTO
- VERIZON ENTERPRISE SOLUTIONS
- PTC INC
- OTHERS
These companies use various strategies such as merger & acquisition, collaboration, partnership and product launch. Whereas, product and service launches is the key strategy adopted by the companies of global IOT Security market.
For Example; In May 2016, Gemalto showcased its connectivity, security and monetization strategy at IoT World 2016 in order to provide IoT security services to their consumer and provide new business opportunities to the enterprises..
In June 2017, Metova, a world leading app, IoT and Development Company, announced its new IoT Security Audit Service which would enable the companies to examine and verify the security of their IoT devices, connected home and embedded systems.
The report covers detailed analysis of companies which comprises of overview, SCOT analysis, product portfolio, strategic initiative, strategic analysis, competitive landscape and market share analysis in global IOT Security market.
Key reasons to buy the report:
- The report includes market estimation, forecast and analysis for the year 2016-2023
- Report includes detailed analysis of different segments such as security, solutions and applications of IOT Security market.
- Identify and understand the strengths, opportunities, challenges and threats of global IOT security market.
- Covers details analysis of Porters 5 force model and other strategic models and also covers revenues, market share analysis, competitive landscape analysis of major players of global IOT security market
- Detailed analysis of various regulatory policies which affect the global IOT Security market.
How we are different from others:
At Occams we provide an extensive portfolio which is comprehensive market analysis along with the market size, market share, and market segmentation. Our report on global IOT Security market offers detailed analysis of strategic models such as investment vs. adoption model, see-saw analysis and others strategic models. Also, the report contains the detailed analysis of application, adoption scenario and decision support for each segment. The report discusses competitive landscape of global IOT Security market, with giving extensive SCOT analysis of key companies.
Key findings of the global IOT security market:
- The global IOT security is expected to rise with a CAGR of 38% during the forecast period 2016-2023.
- The key factor contributing to the growth of global IOT security market is the increasing number of ransomware attacks on the IOT devices due to which there has been a vast increase in the usage of IOT security solutions.
- North America has the highest market share for IOT security. Asia Pacific is the fastest growing region in the global IOT security market.
- Cloud security is the leading segment and is expected to grow at a CAGR of over 25% during the forecast period.
- Product and service launches are the key strategy adopted by the companies of global IOT Security market.


